Why Choose GVO for your Scans?
At GVO, we understand that in today's digital landscape, safeguarding your organization's assets is paramount. Here's why partnering with us is the smart choice:
1. Certified Expertise
Our team comprises seasoned professionals holding industry-recognized certifications, ensuring that your security assessments are conducted with the highest level of proficiency and ethical standards.
2. Comprehensive Services
We offer a full spectrum of security assessments, including:
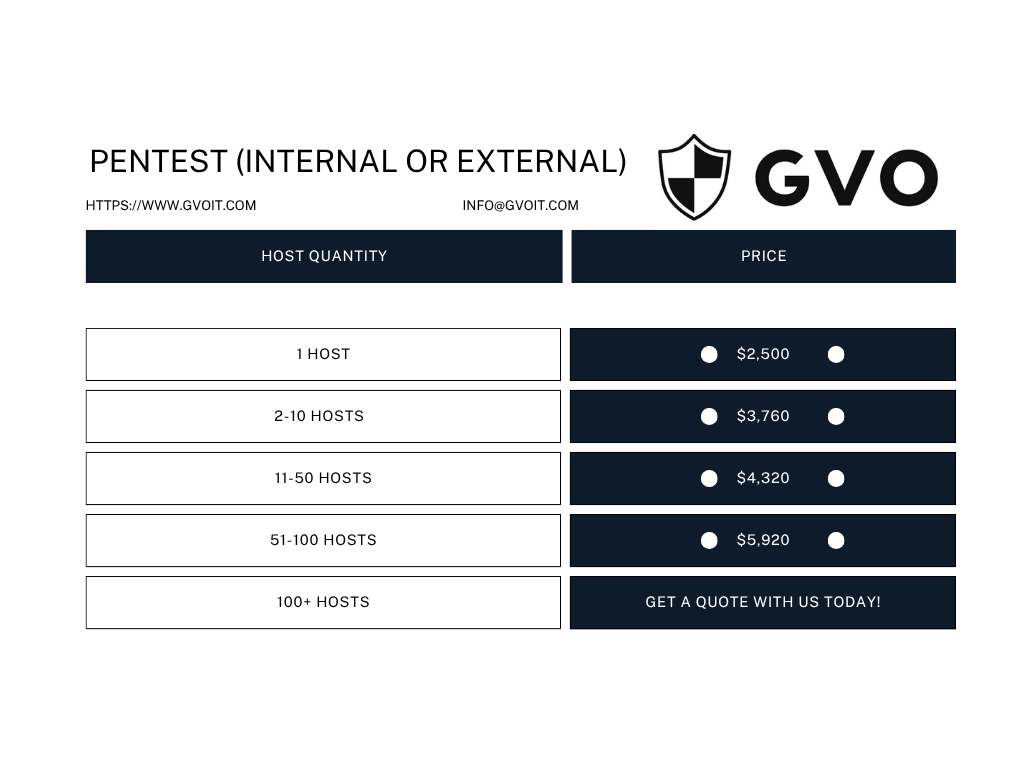
Internal and External Vulnerability Scans
Internal and External Penetration Testing
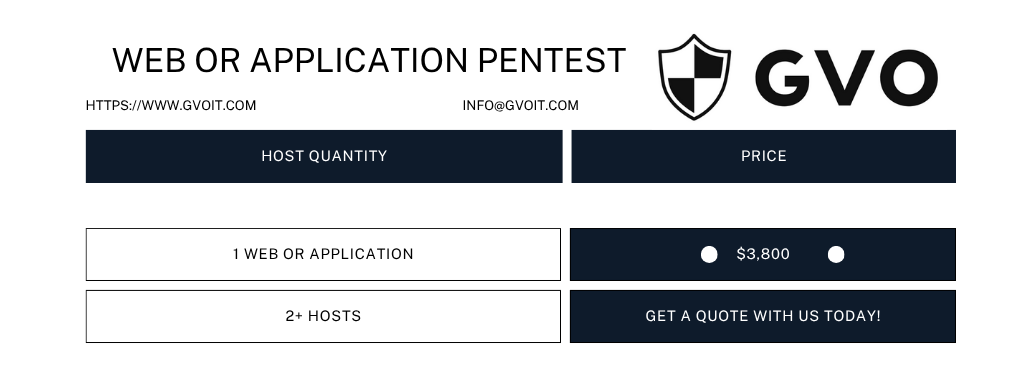
Application Penetration Testing
Each service is meticulously designed to identify and address potential vulnerabilities across your organization's infrastructure.
3. Quality and Precision
Our assessments go beyond surface-level evaluations. We delve deep into your systems to uncover hidden weaknesses, providing detailed reports and actionable recommendations to fortify your security posture.
4. Client-Centric Approach
Your organization's unique needs are at the forefront of our services. We tailor our assessments to align with your specific requirements, ensuring relevant and effective security solutions.
5. Commitment to Compliance
Navigating the complex landscape of regulatory requirements can be daunting. Our services are designed to assist you in achieving and maintaining compliance with industry standards, providing peace of mind and operational assurance.
6. Transparent Reporting
We believe in clear communication. Our comprehensive reports demystify technical findings, offering straightforward insights and prioritized action plans to enhance your security measures.
7. Proven Track Record
Our history of successful engagements across various industries speaks to our reliability and effectiveness in delivering top-tier cybersecurity solutions.
Take the Next Step
Don't wait for a security breach to take action. Contact us today to receive a personalized quote and discover how GVO can empower your organization to stay ahead of cyber threats.